
Company Demands Passwords From An Employee That Was Fired 4 Years Ago, Threatens To Sue Him
Sometimes work-related problems can haunt you even years after leaving the company. It might be consequences of the stress it caused, former colleagues reaching out, or, in some cases, a lawsuit coming out of the blue.
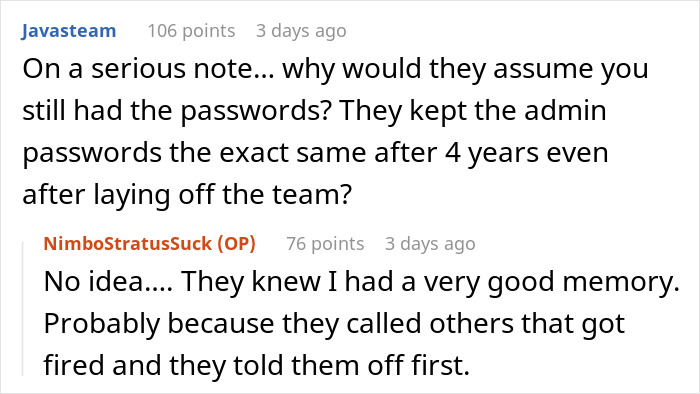
Redditor u/NimboStratusSuck told the ‘Antiwork’ community about his former company wanting to sue him. Their reasons for that seem questionable, as they request specific information which the redditor likely shouldn’t even have anymore. To add insult to injury, it’s been four years since he’s been let go.
Some employers might reveal their true colors years after you leave the workplace
Image credits: Djordje Petrovic (not the actual photo)
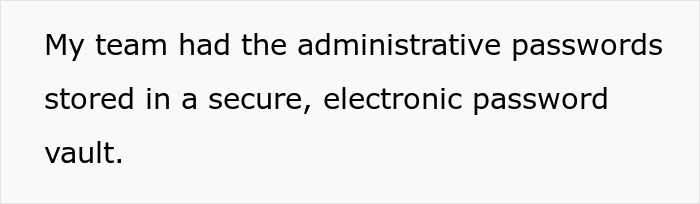
This company asked their former employee to provide password information after he’s been gone for four years
Image credits: Jack Sparrow (not the actual photo)
Image credits: NimboStratusSuck
Image credits: Kampus production (not the actual photo)
Certain safety measures could have prevented the OP from disclosing the passwords even if he wanted to
Oftentimes, certain laws or employment agreements regulate the way a company’s information is handled. It clearly describes the dos and don’ts both while working and after leaving the place. This is necessary to ensure the security of the company’s data, and can help to avoid or solve related conflicts that might arise.
Whether they’re stated on the contract of employment, a non-disclosure agreement, or elsewhere, such rules might require departing employees to refrain from sharing confidential information, such as trade secrets, client data, or logins. The OP might have been obliged to erase the passwords from his memory the second he walked out the door.
Another step companies often take when an employee is leaving is changing their passwords, which might be especially important if it was a high-ranking or a long-term one. According to Impact, disabling the password should be the first thing on the to-do list, as the former team member can act however they see fit until it’s done.
Misuse of private material might pose a serious threat to the company. Redentry revealed that when it comes to cybersecurity, users who have access to sensitive information are the biggest risk. In addition to that, according to Business Wire, roughly 12% of departing employees take such information with them when leaving the workplace.
Image credits: Mike MacKenzie (not the actual photo)
Clear policies when it comes to passwords are crucial in order to avoid any cybersecurity breaches
Such risks can lead to cybersecurity breaches, which are not a rare occurrence. When it comes to small businesses, for example, in 2020 alone, they endured over 700,000 attacks. Companies are not the only ones who are at risk, though. In 2022, roughly 422 million people were affected by some sort of data compromises.
Some cybersecurity experts advise people to change their passwords at least once every three months. Others believe that if you have a strong one, there is no need to alter it unless you suspect it’s been compromised. Be that as it may, most of them would agree that it should at least be more creative than 123456. Sadly, it is arguably the second most common password, outrun only by the word ‘password’ itself.
It’s unclear whether it was the sequence of the first few numbers or something slightly more complex that the OP had to memorize. However, he said he couldn’t provide the company with the passwords anymore. It’s been four years, after all.
Bored Panda has reached out to the redditor u/NimboStratusSuck via the comment section of their post, and we’ll update the article once we hear back from him.
People didn’t hold back from commenting and provided opinions, as well as suggestions on how to reply to the company
I had a similar interaction in my last job, guy was made redundant and was allowed to keep his laptop after it had been wiped and rebuilt so there was no data on it. After 2 years he calls me wanting to know the BIOS password. Had to explain several times that there was no BIOS password when he took the laptop so what makes him think I would know a password I never set. "You're in IT though". Yes but I am not a sorcerer. I ask out of curiosity I ask him when he set this password. The reply was he didn't but it appeared after he spilt water all over it. Cue a lot of internal screaming and I had to end the call.
If you can remember the passwords 4 years later, they weren't very good passwords.
Yup. "Have you tried using password123? No? Then I can't help you."
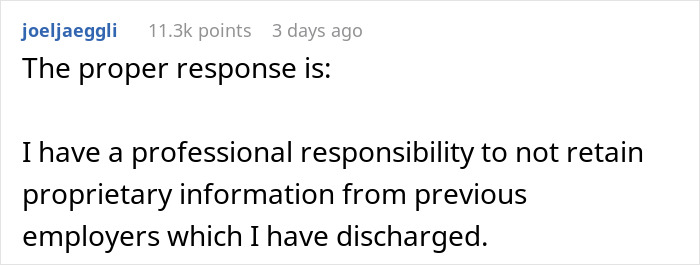
Load More Replies...Gentlemen, due to high ethical and professional standards, I do not possess and have not retained any proprietary information about your company. I do, however, have a reasonably sized bag of silicon dioxide that you are welcome to beat upon in the hopes that it will divulge the information you seek.
"Okay, wow. 4 years. Y'all haven't changed the company passwords in 4 years? Hey, I think I left my lunch in the fridge - is it still in there? What about that open container of milk? Just, wow. Listen, I suggest you put out an Amber alert for those passwords. They are old enough to start preschool. Tell the police you are missing a bunch of 4 year olds. Get the public involved, make the evening news. Oh, and thank you! Have I got a story for the guys at the pub tonight."
The correct response is that OP doesn’t hold any information from after he left the job - this is an obligation set in really any contract whether employee or supplier. I’m confused though - they fired him and never replaced him? They just straight up haven’t been properly maintaining their network security? Yikes
So you give them the password and they sue you for stealing company secrets. Heads you lose, tails they win.
So many people throw around the term "I'm going to sue you" that it really has no credibility any more as almost no one follows through with it
Counter sue and ask for all attorney and court costs. Why not make a little extra from their idiocy?
I had a similar interaction in my last job, guy was made redundant and was allowed to keep his laptop after it had been wiped and rebuilt so there was no data on it. After 2 years he calls me wanting to know the BIOS password. Had to explain several times that there was no BIOS password when he took the laptop so what makes him think I would know a password I never set. "You're in IT though". Yes but I am not a sorcerer. I ask out of curiosity I ask him when he set this password. The reply was he didn't but it appeared after he spilt water all over it. Cue a lot of internal screaming and I had to end the call.
If you can remember the passwords 4 years later, they weren't very good passwords.
Yup. "Have you tried using password123? No? Then I can't help you."
Load More Replies...Gentlemen, due to high ethical and professional standards, I do not possess and have not retained any proprietary information about your company. I do, however, have a reasonably sized bag of silicon dioxide that you are welcome to beat upon in the hopes that it will divulge the information you seek.
"Okay, wow. 4 years. Y'all haven't changed the company passwords in 4 years? Hey, I think I left my lunch in the fridge - is it still in there? What about that open container of milk? Just, wow. Listen, I suggest you put out an Amber alert for those passwords. They are old enough to start preschool. Tell the police you are missing a bunch of 4 year olds. Get the public involved, make the evening news. Oh, and thank you! Have I got a story for the guys at the pub tonight."
The correct response is that OP doesn’t hold any information from after he left the job - this is an obligation set in really any contract whether employee or supplier. I’m confused though - they fired him and never replaced him? They just straight up haven’t been properly maintaining their network security? Yikes
So you give them the password and they sue you for stealing company secrets. Heads you lose, tails they win.
So many people throw around the term "I'm going to sue you" that it really has no credibility any more as almost no one follows through with it
Counter sue and ask for all attorney and court costs. Why not make a little extra from their idiocy?

 Dark Mode
Dark Mode 

 No fees, cancel anytime
No fees, cancel anytime 






























































86
25